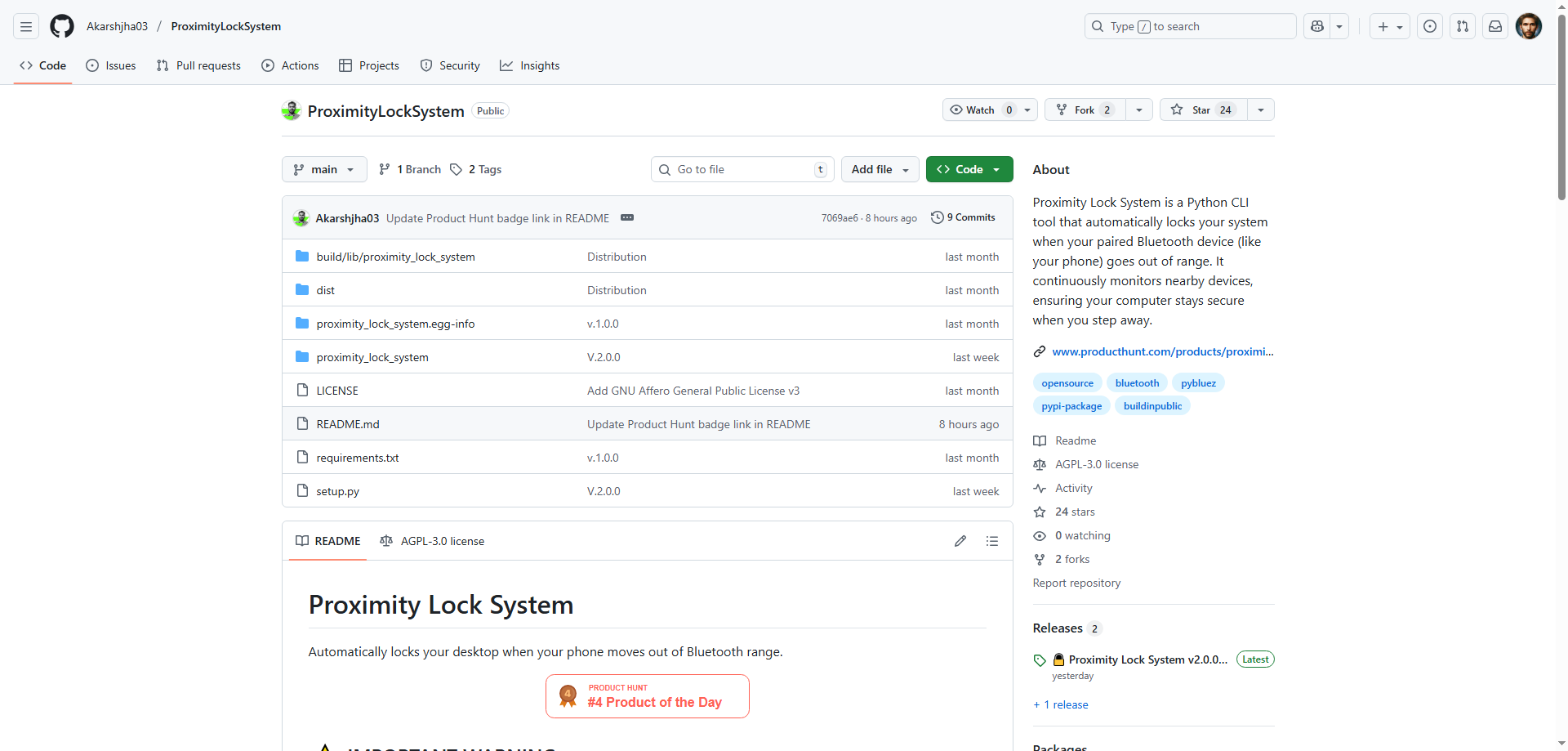
I'll admit it—I'm guilty of the walk-away-without-locking crime. You know the one. You're deep in work, someone calls your name, you pop up from your desk to grab coffee or chat with a colleague, and your computer sits there wide open, displaying your emails, documents, maybe even your embarrassing Spotify playlist. We've all done it. So when I came across Proximity Lock System 2.0, a command-line tool that promises to automatically lock your computer when you walk away with your phone, I was intrigued. Could this simple concept actually solve a real security problem? Let me break it down.
The Creative Concept: Simple Genius or Obvious Solution?
Let's start with the creative angle, because I think there's something genuinely clever here even if it seems straightforward at first glance.
The creative insight behind Proximity Lock System is beautifully simple: you almost never leave your desk without your phone. That device you're addicted to, that you check compulsively, that's practically an extension of your hand—why not leverage that behavioral pattern for security? Your phone becomes your security key without you needing to do anything differently.
What I find creatively interesting is how this flips the traditional security paradigm. Most security measures require active participation. You have to remember to lock your screen. You have to type passwords. You have to authenticate. These are all actions that depend on your attention and memory, both of which are unreliable when you're rushing off to a meeting or distracted by a conversation.
Proximity Lock System takes a passive approach to security. Instead of asking you to do something, it monitors what you're already doing—carrying your phone—and responds accordingly. That's not just convenient; it's psychologically smart. The best security is security you don't have to think about.
The command-line interface is a creative choice worth noting too. In an age of polished GUI apps, going command-line is either brilliantly minimalist or potentially limiting. For technical users who live in terminals, this feels natural and powerful. You're probably already comfortable with command-line tools, and another one fits seamlessly into your workflow. But for non-technical users? That's a different story, which I'll get to later.
The continuous Bluetooth monitoring is technically creative because it's using existing technology in a new way. Bluetooth has been around forever, primarily for audio and file transfer. Repurposing it as a proximity sensor for security is lateral thinking at its best. You're not buying new hardware or setting up complex infrastructure. You're just using the Bluetooth already in your phone and computer.
The customizable distance threshold shows creative consideration for real-world usage. Not everyone's workspace is the same. In an open office, you might want the lock to trigger after just a few meters. At home, you might set a larger radius so it doesn't lock every time you step into the kitchen. This personalization acknowledges that security needs aren't one-size-fits-all.
However, I do see a creative limitation. The product relies entirely on one device—your phone. What if you leave your phone at your desk but walk away? What if your phone battery dies? The single point of dependency is elegant but also potentially fragile.
Disruption Analysis: Can This Replace What We Already Use?
Now let's talk about whether Proximity Lock System 2.0 can actually disrupt or replace existing security solutions. This requires looking at what currently exists and whether this tool offers enough improvement to change behavior.
The most direct comparison is to built-in operating system features. Both Mac and Windows have auto-lock features that trigger after a period of inactivity. You can set your computer to lock after 2 minutes, 5 minutes, or whatever you prefer. These are good enough solutions for many people. The question is: does proximity-based locking offer enough advantage over time-based locking to warrant switching?
The answer is: sometimes yes, sometimes no. Time-based locking is frustrating because it can trigger when you're still at your desk but thinking, reading, or on a call without touching your keyboard. You're actively working, but the computer thinks you're gone. Proximity Lock System doesn't have this problem—if you're at your desk with your phone, the computer stays unlocked regardless of keyboard activity.
Conversely, time-based locking doesn't require Bluetooth setup, phone proximity, or any additional configuration. It just works. For many users, the convenience of the existing solution outweighs the precision of the new one.
There are also dedicated security solutions like Bluetooth unlock devices, proximity badges, and even facial recognition systems. These already exist in enterprise environments. Proximity Lock System enters a space that has competitors, though it does so as an open-source command-line tool rather than a paid enterprise product. That's disruptive in the sense of offering similar functionality for free, but not disruptive in offering fundamentally new capabilities.
Where I see genuine disruption potential is in the prosumer and developer market. Software developers, system administrators, and tech professionals who work in security-conscious environments but don't have enterprise security budgets could find real value here. A free, open-source tool that adds a layer of automatic security without monthly fees or complex deployment is attractive.
The automation aspect is potentially disruptive to behavior. Right now, security-conscious people develop habits—always pressing Win+L before standing up, always clicking the lock button on Mac. These habits, while good, are cognitive overhead. Proximity Lock System could disrupt this mental burden by making security unconscious. Your computer's security becomes tied to your behavior, not your memory.
But full disruption is unlikely for several reasons. First, the command-line interface immediately limits the user base. Most people don't open terminal windows, and asking them to start for security feels like a non-starter. Second, the reliance on Bluetooth means both devices need Bluetooth enabled and paired, which introduces complexity and potential battery drain. Third, Bluetooth range isn't precise—walls, interference, and other factors can cause inconsistent distance detection.
My honest assessment: Proximity Lock System won't replace existing solutions broadly, but it will complement them for technical users who want additional security layers. It's a supplement, not a replacement.
User Acceptance: Do People Really Need This?
Let's get into whether there's genuine demand for Proximity Lock System and who would actually adopt it.
The use cases presented are compelling on paper. Office workers rushing to meetings, remote workers stepping away from their desks, freelancers in coffee shops—these are real scenarios where forgetting to lock your screen poses genuine risks. Information security breaches, privacy violations, and even data theft can result from unlocked computers. The risk is real.
But is the solution what people want? Let me consider different user segments.
For IT professionals and developers, acceptance should be high. These users understand security risks intimately. They're comfortable with command-line tools. They appreciate open-source solutions they can inspect and potentially modify. The 194 upvotes and 33 discussions on Product Hunt suggest technical users are interested. This is the core audience, and they'll likely embrace it.
For corporate employees in regulated industries—finance, healthcare, legal—automatic screen locking isn't optional; it's mandatory. These environments often have strict policies about unattended computers. Proximity Lock System could be valuable here, but corporate IT departments are notoriously conservative about installing unapproved tools. Without enterprise-grade support, compliance certifications, and IT department endorsement, adoption in corporate environments will be limited.
For casual users—students, general consumers, non-technical professionals—acceptance is questionable. The command-line interface is the primary barrier. Most people don't know what a command line is, let alone feel comfortable using it. Even if they understand the concept and want the benefit, the implementation method is intimidating.
The Bluetooth requirement adds another acceptance hurdle. Not everyone keeps Bluetooth enabled due to battery concerns. Pairing devices, while not difficult, is one more setup step that casual users might not complete. And if the system triggers false locks because of Bluetooth range issues, user frustration could lead to abandonment.
Geographic and workplace context matters too. In some cultures, leaving your computer unlocked at your desk isn't seen as a major issue because workplace norms discourage touching others' equipment. In more security-conscious or less trusting environments, automatic locking becomes more valuable. User acceptance will vary by context.
One strong acceptance factor is the pain point authenticity. Almost everyone has experienced the moment of realizing they left their computer unlocked with sensitive information visible. That "oh no" feeling when you rush back to your desk hoping no one saw your screen—that's a universal experience. Products that address genuine pain points have higher acceptance rates.
The specific use case of coffee shop workers resonates strongly with me. Public environments represent real security risks. Having your laptop auto-lock when you step away to order another coffee or use the restroom provides peace of mind that's genuinely valuable.
Overall, I predict modest but dedicated user acceptance among technical users, with limited mainstream adoption unless the team develops a more accessible interface.
Survival Rating: 3.5 out of 5 Stars
After careful evaluation, I'm rating Proximity Lock System 2.0's one-year survival prospects at 3.5 out of 5 stars. Here's my detailed reasoning.
Opportunities for Success
First, the open-source model is advantageous. Without needing to generate immediate revenue, the project can grow organically. GitHub stars, community contributions, and word-of-mouth marketing can sustain open-source projects for years. The 33 discussions on Product Hunt show community engagement, which is positive.
Second, the security consciousness trend is growing. With increasing remote work, data breaches making headlines, and general privacy awareness rising, tools that enhance personal security are timely. Proximity Lock System rides this wave of security consciousness.
Third, the technical audience is loyal. Developer tools often develop cult followings. If Proximity Lock System becomes known in developer circles as a reliable, useful tool, recommendation and adoption within that community could be strong. Technical users also contribute improvements, report bugs, and create tutorials—all of which help the project grow.
Fourth, the concept is extensible. While currently focused on screen locking, the proximity detection could theoretically expand to other actions—automatically pausing music, activating privacy screens, triggering backup routines. That extensibility gives the project growth potential.
Fifth, cross-platform compatibility (if achieved—the keywords mention Mac and Windows) broadens the potential user base. Platform-agnostic tools have larger markets.
Risks to Consider
The biggest risk is the limited user interface. Command-line tools have inherent adoption ceilings. Unless the team develops a GUI wrapper or simplified installation process, mainstream adoption won't happen. If the project remains developer-focused, it survives but doesn't grow significantly.
Bluetooth reliability is a technical risk. Inconsistent Bluetooth behavior—false locks, failure to lock, battery drain—could frustrate users enough to abandon the tool. Technical execution must be flawless, and Bluetooth is notoriously finicky.
Competition from built-in features is real. If Apple or Microsoft decides to add proximity-based locking natively (using their own ecosystem devices like Apple Watch or Android phones), this third-party solution becomes redundant. Platform owners can easily commoditize innovative features.
Maintenance sustainability is a concern for open-source projects. Without dedicated maintainers or funding, projects can become abandoned. Security tools require regular updates to address vulnerabilities and platform changes. Long-term maintenance commitment is essential.
User behavior change is harder than expected. Even beneficial tools get abandoned because changing habits is difficult. Users might install Proximity Lock System, use it for a week, find the setup annoying or experience false triggers, and uninstall. Sustained usage requires seamless experience.
Finally, there's the distraction risk. If users rely on automatic locking and the system fails—Bluetooth disconnects, phone battery dies—they might be less vigilant about manual locking. False sense of security could lead to worse outcomes than before.
My Bottom Line
Proximity Lock System 2.0 solves a real problem with a clever approach. The concept of using your phone's proximity as a security trigger is sound and addresses genuine security gaps. For technical users comfortable with command-line tools, this could become a valued part of their security setup.
However, the product's current form limits its reach. The 3.5-star rating reflects my belief that it will survive and find its niche audience, but won't achieve broad adoption without significant interface improvements. It's a solid tool for a specific user type, not a mainstream solution.
If the development team can build a user-friendly GUI, perhaps package it as a proper application with simple setup wizards, and market it effectively to security-conscious but non-technical users, the rating could improve significantly. Without those evolutions, Proximity Lock System remains a developer's tool—useful, appreciated by those who use it, but ultimately limited in impact.
For now, if you're a technical user who works in environments where unattended computers pose security risks, and you're comfortable with command-line setup, Proximity Lock System 2.0 is worth your attention. Just don't expect your non-technical friends to start using it anytime soon.
The core idea is solid. The execution is functional. The market fit is narrow but real. That's a recipe for survival, if not dominance.